You can query the Ampersand Auth backend through a REST API. This can be used for various operations such as creating new users, signing in existing ones and editing or deleting these users.
Convenient authentication management page on ampersand cloud
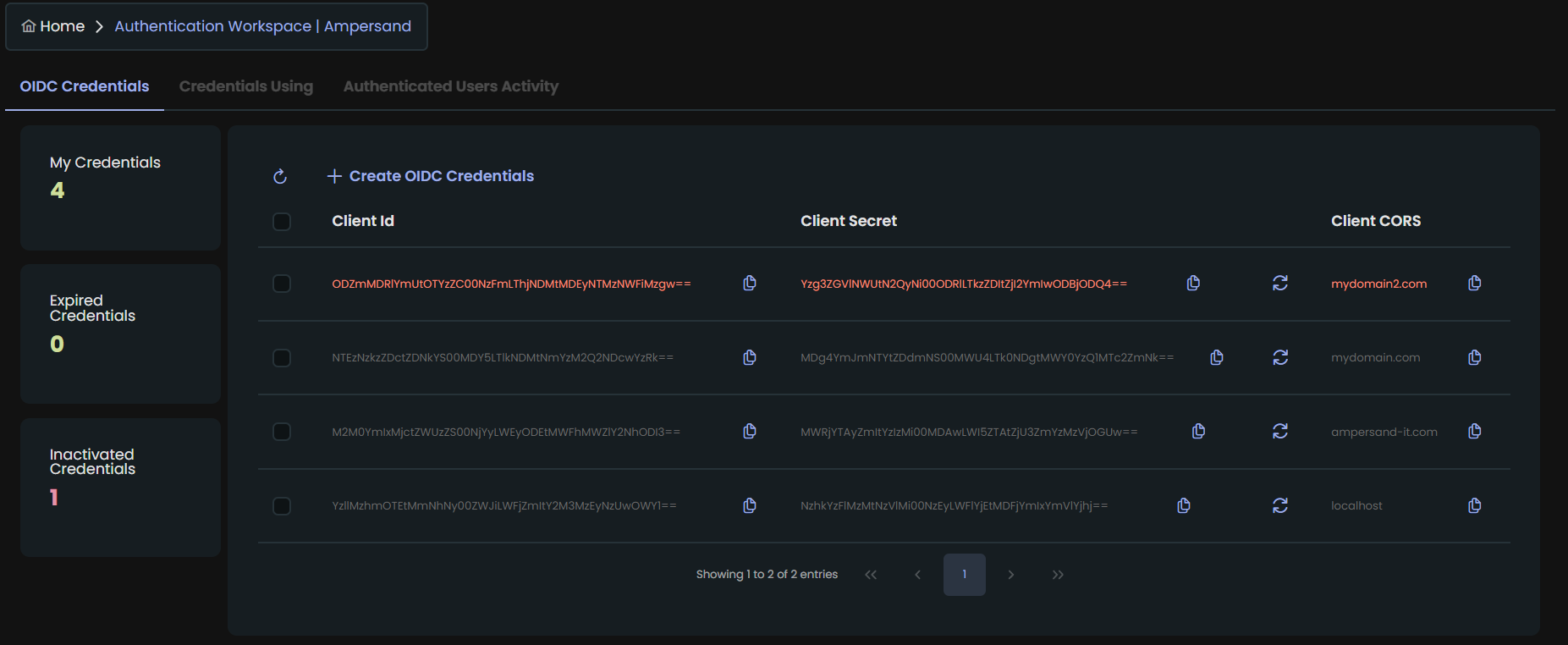
Our Authentication fully based on OAuth 2.0 JWT Bearer Token Specefication
OAuth 2.0 is a framework for securing API access by allowing third-party applications (clients) to obtain limited access to user resources on a server (resource server) on behalf of the user. It involves several actors: the client application, the resource owner (user), the authorization server, and the resource server.
- Authorization Grant:OAuth 2.0 starts with the client application requesting authorization from the user to access their resources. The client application receives an authorization grant (such as a password) from the authorization server.
- Token Request:
The client application exchanges the authorization grant for an access token by making a token request to the authorization server. In the context of JWT authentication, the access token generated by the authorization server is a JWT.
- JWT Token Generation:
The authorization server generates a JWT that contains information about the user and the access privileges granted to the client. This JWT typically includes the user's identity, scope of access, and other relevant claims.
- Token Transmission:
The client application receives the JWT access token and includes it in the headers of API requests to the resource server. The token is sent in the "Authorization" header using the "Bearer" scheme.
Authorization: Bearer [YOUR_JWT_ACCESS_TOKEN] - Resource Server Validation:
The resource server receives the API request and validates the JWT access token's signature using the public key associated with the authorization server. If the signature is valid, the resource server trusts the information in the token and processes the request.
- Token Expiry and Refresh:
JWT access tokens often have an expiration time. If the token expires, the client can request a new one using a refresh token if it was issued during the initial authentication process.
- User Consent and Authorization:
In OAuth 2.0, the initial authorization step involves the user granting consent to the client application. It's important to document how the user interacts with the authorization server to grant or deny access.